mirror of
https://github.com/cliffe/SecGen.git
synced 2026-02-20 13:50:45 +00:00
CyBOK readme index
This commit is contained in:
360
README-CyBOK-Lecture-Videos.md
Normal file
360
README-CyBOK-Lecture-Videos.md
Normal file
@@ -0,0 +1,360 @@
|
||||
# Lecture Videos
|
||||
|
||||
This file is an autogenerated index of the lecture videos referenced by scenarios -- with CyBOK metadata.
|
||||
|
||||
|
||||
|
||||
## A video!
|
||||
by Somebody
|
||||
|
||||
|
||||
![thumbnail]()
|
||||
www.example.com
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| OSV | OS Security Principles | security models |
|
||||
|
||||
## A video!
|
||||
by Somebody
|
||||
|
||||
|
||||
![thumbnail]()
|
||||
www.example.com
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| OSV | OS Security Principles | security models |
|
||||
|
||||
|
||||
|
||||
|
||||
## User accounts and Linux
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/2I_JSdTu-oI
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | user authentication |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["authentication and identification", "Linux authentication", "Types of user accounts"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Passwords Part 1 Hashing and salt
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/pGcJEML1mRo
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["user authentication", "Cryptography and authentication (hashes and attacks against authentication schemes / passwords)"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["authentication and identification", "Linux authentication"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Passwords Part 2 Attacks and Countermeasures
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/icC2Zrno_uM
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["user authentication", "Cryptography and authentication (hashes and attacks against authentication schemes / passwords)"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["authentication and identification", "Linux authentication"] |
|
||||
|
||||
|
||||
|
||||
|
||||
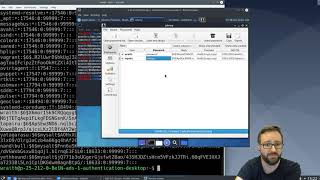
## Password cracking with Johnny
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/Wrg6XZu6Luw
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["user authentication", "Cryptography and authentication (hashes and attacks against authentication schemes / passwords)"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["authentication and identification", "Linux authentication"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Authentication
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/z4L6Yv5ry1A
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "user authentication", "facets of authentication"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["authentication and identification", "Linux authentication"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Biometrics
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/-zcnfmoLjYI
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "user authentication", "facets of authentication", "AUTHENTICATION - BIOMETRICS"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Authentication Tokens and One-Time Passwords
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/xHs3LB4Yyrk
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "user authentication", "facets of authentication", "AUTHENTICATION - OTP (ONE-TIME PASSWORD)", "AUTHENTICATION - TOKENS"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Network-based Authentication (SSO, AD, LDAP, Kerberos)
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/c2dPdQmaVyo
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "authentication in distributed systems", "user authentication", "Network based-authentication with heterogeneous Linux and Windows networks"] |
|
||||
| AAA | Authorisation | ["AUTHORIZATION - SSO (SINGLE SIGN-ON)", "AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL)", "AUTHENTICATION - KERBEROS", "ACTIVE DIRECTORY DOMAIN SERVICES (ADDS)"] |
|
||||
| AAA | Access Control in Distributed Systems | ["core concepts", "federated access control"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Lightweight Directory Access Protocol (LDAP)
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/dCBabesIXo8
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "authentication in distributed systems", "user authentication"] |
|
||||
| AAA | Authorisation | ["theory", "Network based-authentication with heterogeneous Linux and Windows networks", "AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL)"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Kerberos overview
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/rhdcxhSDqp4
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "authentication in distributed systems", "user authentication", "Network based-authentication with heterogeneous Linux and Windows networks"] |
|
||||
| AAA | Authorisation | AUTHENTICATION - KERBEROS |
|
||||
|
||||
|
||||
|
||||
|
||||
## Active Directory
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||

|
||||
|
||||
https://youtu.be/PCXK2cK8tpE
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | ["identity management", "authentication in distributed systems", "user authentication", "Network based-authentication with heterogeneous Linux and Windows networks"] |
|
||||
| AAA | Authorisation | ["AUTHORIZATION - SSO (SINGLE SIGN-ON)", "AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL)", "AUTHENTICATION - KERBEROS", "ACTIVE DIRECTORY DOMAIN SERVICES (ADDS)"] |
|
||||
| AAA | Access Control in Distributed Systems | ["core concepts", "federated access control"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Access Controls: Introduction
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/yWJyZEFbchQ
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "enforcing access control", "theory"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | Access controls and operating systems |
|
||||
| OSVS | Role of Operating Systems | ["mediation", "TRUSTED COMPUTING BASE (TCB)", "REFERENCE MONITOR"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Unix File Permissions
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/i0kO_3ExJv4
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "enforcing access control", "ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL)"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["Access controls and operating systems", "Linux security model", "Unix File Permissions", "filesystems, inodes, and commands"] |
|
||||
| OSVS | Role of Operating Systems | mediation |
|
||||
|
||||
|
||||
|
||||
|
||||
## Access Control Models
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/viSkkNB777k
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "theory", "ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL)", "ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL)", "ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL)", "ACCESS CONTROL - ROLE-BASED"] |
|
||||
| OSVS | OS Security Principles | security models |
|
||||
|
||||
|
||||
|
||||
|
||||
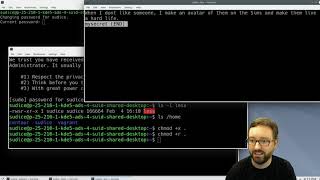
## Special File Permissions SetUID, SetGUI
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/PGHsb3bg_h4
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "Elevated privileges", "Real and effective identity", "Vulnerabilities and attacks on access control misconfigurations"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["Access controls and operating systems", "Linux security model", "Unix File Permissions", "setuid/setgid"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## ACLs and Capabilities
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/Bn3NJhgmdLk
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "ACCESS CONTROL - MATRIX", "ACCESS CONTROL LIST (ACL)", "Vulnerabilities and attacks on access control misconfigurations"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | capabilities |
|
||||
|
||||
|
||||
|
||||
|
||||
## Linux Extended ACLs
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
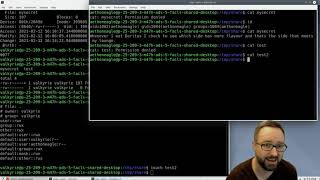
|
||||
|
||||
https://youtu.be/OT7ifs8PkHI
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["access control", "ACCESS CONTROL LIST (ACL)", "Vulnerabilities and attacks on access control misconfigurations"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["Access controls and operating systems", "Linux security model", "Linux Extended Access Control Lists (facl)"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Sandboxing and Virtualisation
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/f4yBcKkb12g
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["SANDBOX", "Application-based access controls: user-based access controls insufficiently limit privileges"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | ["capabilities", "Container-based sandboxes: chroot, Docker", "Rule-based controls: Course grained: Linux capabilities", "System-level sandboxes (complete OS, Qubes), hardware-emulation and paravirtualisation", "Copy on write sandboxes"] |
|
||||
| OSVS | Role of Operating Systems | ["isolation", "CONTAINERS"] |
|
||||
| WMS | Fundamental Concepts and Approaches | ["sandboxing", "permission dialog based access control"] |
|
||||
|
||||
|
||||
|
||||
|
||||
## Rule-based Sandboxing and Mandatory Access Controls
|
||||
by Z. Cliffe Schreuders
|
||||
|
||||
|
||||
|
||||
|
||||
https://youtu.be/Xgs5akM6ayc
|
||||
|
||||
|
||||
| KA | Topics | Keywords |
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ["ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL)", "ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL)", "Application-based access controls: user-based access controls insufficiently limit privileges", "Rule-based sandboxes", "System call interposition", "Integrity level access controls"] |
|
||||
| OSVS | Primitives for Isolation and Mediation | Rule-based controls: Fine grained: AppArmor |
|
||||
| SS | Mitigating Exploitation | limiting privileges |
|
||||
|
||||
|
||||
|
||||
716
README-CyBOK-Scenarios-Indexed.md
Normal file
716
README-CyBOK-Scenarios-Indexed.md
Normal file
@@ -0,0 +1,716 @@
|
||||
This file is an autogenerated index and cross referencing of all the scenarios that have CyBOK metadata.
|
||||
|
||||
# By Knowledge Area
|
||||
|
||||
|
||||
|
||||
# AAA
|
||||
|
||||
## AAA Scenarios
|
||||
examples/cybok_example.xml</br>examples/cybok_example_no_systems.xml</br>labs/authentication_and_access_controls/ads_1_authentication.xml</br>labs/authentication_and_access_controls/ads_2_pam.xml</br>labs/authentication_and_access_controls/ads_3_access_controls.xml</br>labs/authentication_and_access_controls/ads_4_suid.xml</br>labs/authentication_and_access_controls/ads_5_facls.xml</br>labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml</br>labs/labtainers/file-integrity.xml</br>labs/labtainers/ldap.xml</br>labs/labtainers/macs-hash.xml</br>labs/labtainers/nix-commands.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/radius.xml</br>labs/labtainers/setuid-env.xml</br>labs/response_and_investigation/1_integrity_protection.xml</br>labs/response_and_investigation/7_live_analysis.xml</br>labs/response_and_investigation/8_dead_analysis.xml
|
||||
|
||||
## AAA Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Authorisation | examples/cybok_example.xml</br>examples/cybok_example_no_systems.xml</br>labs/authentication_and_access_controls/ads_3_access_controls.xml</br>labs/authentication_and_access_controls/ads_4_suid.xml</br>labs/authentication_and_access_controls/ads_5_facls.xml</br>labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml</br>labs/labtainers/ldap.xml</br>labs/labtainers/nix-commands.xml</br>labs/labtainers/setuid-env.xml</br>labs/response_and_investigation/1_integrity_protection.xml
|
||||
Authentication | labs/authentication_and_access_controls/ads_1_authentication.xml</br>labs/authentication_and_access_controls/ads_2_pam.xml</br>labs/labtainers/file-integrity.xml</br>labs/labtainers/ldap.xml</br>labs/labtainers/macs-hash.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/radius.xml
|
||||
Accountability | labs/response_and_investigation/7_live_analysis.xml</br>labs/response_and_investigation/8_dead_analysis.xml
|
||||
|
||||
# C
|
||||
|
||||
## C Scenarios
|
||||
examples/cybok_example.xml</br>examples/cybok_example_no_systems.xml</br>labs/labtainers/macs-hash.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/pubkey.xml</br>labs/labtainers/ssh-agent.xml</br>labs/labtainers/sshlab.xml</br>labs/labtainers/ssl.xml
|
||||
|
||||
## C Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Cryptography | examples/cybok_example.xml</br>examples/cybok_example_no_systems.xml
|
||||
Public-Key Cryptography | labs/labtainers/macs-hash.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/ssh-agent.xml</br>labs/labtainers/sshlab.xml</br>labs/labtainers/ssl.xml
|
||||
Schemes | labs/labtainers/pubkey.xml
|
||||
|
||||
# OSVS
|
||||
|
||||
## OSVS Scenarios
|
||||
labs/authentication_and_access_controls/ads_1_authentication.xml</br>labs/authentication_and_access_controls/ads_2_pam.xml</br>labs/authentication_and_access_controls/ads_3_access_controls.xml</br>labs/authentication_and_access_controls/ads_4_suid.xml</br>labs/authentication_and_access_controls/ads_5_facls.xml</br>labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml</br>labs/labtainers/capabilities.xml</br>labs/labtainers/setuid-env.xml</br>labs/response_and_investigation/1_integrity_protection.xml</br>labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/7_live_analysis.xml
|
||||
|
||||
## OSVS Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Primitives for Isolation and Mediation | labs/authentication_and_access_controls/ads_1_authentication.xml</br>labs/authentication_and_access_controls/ads_2_pam.xml</br>labs/authentication_and_access_controls/ads_3_access_controls.xml</br>labs/authentication_and_access_controls/ads_4_suid.xml</br>labs/authentication_and_access_controls/ads_5_facls.xml</br>labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml</br>labs/labtainers/capabilities.xml</br>labs/labtainers/setuid-env.xml</br>labs/response_and_investigation/1_integrity_protection.xml
|
||||
Role of Operating Systems | labs/authentication_and_access_controls/ads_3_access_controls.xml</br>labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml
|
||||
OS Hardening | labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/7_live_analysis.xml
|
||||
|
||||
# WMS
|
||||
|
||||
## WMS Scenarios
|
||||
labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/labtainers/sql-inject.xml</br>labs/web_security/websec_lab.xml
|
||||
|
||||
## WMS Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Fundamental Concepts and Approaches | labs/authentication_and_access_controls/ads_6_containers.xml</br>labs/web_security/websec_lab.xml
|
||||
Server-Side Vulnerabilities and Mitigations | labs/labtainers/sql-inject.xml</br>labs/web_security/websec_lab.xml
|
||||
Client-Side Vulnerabilities and Mitigations | labs/web_security/websec_lab.xml
|
||||
|
||||
# SS
|
||||
|
||||
## SS Scenarios
|
||||
labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/labtainers/bufoverflow.xml</br>labs/labtainers/formatstring.xml</br>labs/labtainers/pass-crack.xml</br>labs/labtainers/retlibc.xml</br>labs/labtainers/sql-inject.xml</br>labs/software_security_exploitation/1_c_asm_iof.xml</br>labs/software_security_exploitation/2_race_conditions_format_str.xml</br>labs/software_security_exploitation/3_bug_hunting_and_fuzzing.xml</br>labs/software_security_exploitation/4_exploit_development.xml</br>labs/software_security_exploitation/5_linux_bof_format.xml</br>labs/software_security_exploitation/6_linux_stack_bof.xml</br>labs/software_security_exploitation/7_linux_nx_bypass.xml</br>labs/software_security_exploitation/8_linux_aslr_bypass.xml</br>labs/web_security/websec_lab.xml
|
||||
|
||||
## SS Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Mitigating Exploitation | labs/authentication_and_access_controls/ads_7_apparmor.xml</br>labs/labtainers/bufoverflow.xml</br>labs/labtainers/retlibc.xml</br>labs/software_security_exploitation/7_linux_nx_bypass.xml</br>labs/software_security_exploitation/8_linux_aslr_bypass.xml
|
||||
Categories of Vulnerabilities | labs/introducing_attacks/6_exploitation.xml</br>labs/labtainers/bufoverflow.xml</br>labs/labtainers/formatstring.xml</br>labs/labtainers/retlibc.xml</br>labs/labtainers/sql-inject.xml</br>labs/software_security_exploitation/1_c_asm_iof.xml</br>labs/software_security_exploitation/2_race_conditions_format_str.xml</br>labs/software_security_exploitation/4_exploit_development.xml</br>labs/software_security_exploitation/5_linux_bof_format.xml</br>labs/software_security_exploitation/6_linux_stack_bof.xml</br>labs/software_security_exploitation/7_linux_nx_bypass.xml</br>labs/software_security_exploitation/8_linux_aslr_bypass.xml</br>labs/web_security/websec_lab.xml
|
||||
Authentication | labs/labtainers/pass-crack.xml
|
||||
Prevention of Vulnerabilities | labs/labtainers/sql-inject.xml</br>labs/software_security_exploitation/1_c_asm_iof.xml</br>labs/software_security_exploitation/2_race_conditions_format_str.xml</br>labs/web_security/websec_lab.xml
|
||||
Detection of Vulnerabilities | labs/software_security_exploitation/3_bug_hunting_and_fuzzing.xml
|
||||
|
||||
# NS
|
||||
|
||||
## NS Scenarios
|
||||
labs/introducing_attacks/1_intro_linux.xml</br>labs/introducing_attacks/4_dns_footprinting.xml</br>labs/introducing_attacks/5_scanning.xml</br>labs/labtainers/arp-spoof.xml</br>labs/labtainers/denyhost.xml</br>labs/labtainers/dmz-example.xml</br>labs/labtainers/dmz-lab.xml</br>labs/labtainers/iptables-ics.xml</br>labs/labtainers/iptables.xml</br>labs/labtainers/iptables2.xml</br>labs/labtainers/local-dns.xml</br>labs/labtainers/nix-commands.xml</br>labs/labtainers/nmap-discovery.xml</br>labs/labtainers/nmap-ssh.xml</br>labs/labtainers/pcapanalysis.xml</br>labs/labtainers/pubkey.xml</br>labs/labtainers/radius.xml</br>labs/labtainers/remote-dns.xml</br>labs/labtainers/routing-basics.xml</br>labs/labtainers/routing-basics2.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
|
||||
## NS Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Network Protocols and Vulnerability | labs/introducing_attacks/1_intro_linux.xml</br>labs/labtainers/arp-spoof.xml</br>labs/labtainers/local-dns.xml</br>labs/labtainers/remote-dns.xml
|
||||
PENETRATION TESTING | labs/introducing_attacks/4_dns_footprinting.xml</br>labs/introducing_attacks/5_scanning.xml</br>labs/labtainers/nix-commands.xml</br>labs/labtainers/nmap-discovery.xml</br>labs/labtainers/nmap-ssh.xml
|
||||
Network Defence Tools | labs/labtainers/denyhost.xml</br>labs/labtainers/dmz-example.xml</br>labs/labtainers/dmz-lab.xml</br>labs/labtainers/iptables-ics.xml</br>labs/labtainers/iptables.xml</br>labs/labtainers/iptables2.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
Internet Architecture | labs/labtainers/iptables-ics.xml</br>labs/labtainers/iptables.xml</br>labs/labtainers/iptables2.xml</br>labs/labtainers/pubkey.xml</br>labs/labtainers/radius.xml</br>labs/labtainers/routing-basics.xml</br>labs/labtainers/routing-basics2.xml
|
||||
OSI (OPEN SYSTEM INTERCONNECT) MODEL | labs/labtainers/pcapanalysis.xml
|
||||
|
||||
# SOIM
|
||||
|
||||
## SOIM Scenarios
|
||||
labs/introducing_attacks/1_intro_linux.xml</br>labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/introducing_attacks/3_vulnerabilities.xml</br>labs/introducing_attacks/4_dns_footprinting.xml</br>labs/introducing_attacks/5_scanning.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/introducing_attacks/7_post-exploitation.xml</br>labs/introducing_attacks/8_vulnerability_analysis.xml</br>labs/labtainers/arp-spoof.xml</br>labs/labtainers/backups.xml</br>labs/labtainers/backups2.xml</br>labs/labtainers/capabilities.xml</br>labs/labtainers/centos-log.xml</br>labs/labtainers/centos-log2.xml</br>labs/labtainers/cyberciege.xml</br>labs/labtainers/denyhost.xml</br>labs/labtainers/file-integrity.xml</br>labs/labtainers/ldap.xml</br>labs/labtainers/metasploit.xml</br>labs/labtainers/nmap-ssh.xml</br>labs/labtainers/packet-introspection.xml</br>labs/labtainers/pcapanalysis.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/3_backups_and_recovery.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
|
||||
## SOIM Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
PENETRATION TESTING | labs/introducing_attacks/1_intro_linux.xml</br>labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/introducing_attacks/3_vulnerabilities.xml</br>labs/introducing_attacks/4_dns_footprinting.xml</br>labs/introducing_attacks/5_scanning.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/introducing_attacks/7_post-exploitation.xml</br>labs/introducing_attacks/8_vulnerability_analysis.xml</br>labs/labtainers/metasploit.xml
|
||||
Monitor: Data Sources | labs/labtainers/arp-spoof.xml</br>labs/labtainers/capabilities.xml</br>labs/labtainers/centos-log.xml</br>labs/labtainers/centos-log2.xml</br>labs/labtainers/cyberciege.xml</br>labs/labtainers/file-integrity.xml</br>labs/labtainers/ldap.xml</br>labs/labtainers/packet-introspection.xml</br>labs/labtainers/pcapanalysis.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
Execute: Mitigation and Countermeasures | labs/labtainers/backups.xml</br>labs/labtainers/backups2.xml</br>labs/labtainers/denyhost.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/3_backups_and_recovery.xml</br>labs/response_and_investigation/4_ids.xml
|
||||
INCIDENT RESPONSE | labs/labtainers/backups.xml</br>labs/labtainers/backups2.xml
|
||||
CM (CONFIGURATION MANAGEMENT) | labs/labtainers/denyhost.xml</br>labs/labtainers/nmap-ssh.xml
|
||||
Analyse: Analysis Methods | labs/labtainers/snort.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
|
||||
# MAT
|
||||
|
||||
## MAT Scenarios
|
||||
labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/introducing_attacks/3_vulnerabilities.xml</br>labs/introducing_attacks/5_scanning.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/introducing_attacks/7_post-exploitation.xml</br>labs/introducing_attacks/8_vulnerability_analysis.xml</br>labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml</br>labs/labtainers/bufoverflow.xml</br>labs/labtainers/formatstring.xml</br>labs/labtainers/gdblesson.xml</br>labs/labtainers/ida.xml</br>labs/labtainers/metasploit.xml</br>labs/labtainers/retlibc.xml</br>labs/labtainers/snort.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/7_live_analysis.xml</br>labs/response_and_investigation/8_dead_analysis.xml</br>labs/software_and_malware_analysis/1_dynamic_and_static_analysis.xml</br>labs/software_and_malware_analysis/3_c_and_asm.xml</br>labs/software_and_malware_analysis/4_asm.xml</br>labs/software_and_malware_analysis/5_ghidra.xml</br>labs/software_and_malware_analysis/6_ghidra_analysis.xml</br>labs/software_and_malware_analysis/6_ghidra_with_live_malware_samples.xml</br>labs/software_and_malware_analysis/7_dynamic.xml</br>labs/software_and_malware_analysis/8_anti_sre.xml</br>labs/software_and_malware_analysis/9_malware_behaviour.xml</br>labs/software_security_exploitation/4_exploit_development.xml</br>labs/software_security_exploitation/5_linux_bof_format.xml</br>labs/software_security_exploitation/6_linux_stack_bof.xml</br>labs/software_security_exploitation/7_linux_nx_bypass.xml</br>labs/software_security_exploitation/8_linux_aslr_bypass.xml
|
||||
|
||||
## MAT Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Malware Taxonomy | labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/software_and_malware_analysis/1_dynamic_and_static_analysis.xml</br>labs/software_and_malware_analysis/9_malware_behaviour.xml
|
||||
Malware Analysis | labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/labtainers/gdblesson.xml</br>labs/labtainers/ida.xml</br>labs/software_and_malware_analysis/1_dynamic_and_static_analysis.xml</br>labs/software_and_malware_analysis/3_c_and_asm.xml</br>labs/software_and_malware_analysis/4_asm.xml</br>labs/software_and_malware_analysis/5_ghidra.xml</br>labs/software_and_malware_analysis/6_ghidra_analysis.xml</br>labs/software_and_malware_analysis/6_ghidra_with_live_malware_samples.xml</br>labs/software_and_malware_analysis/7_dynamic.xml</br>labs/software_and_malware_analysis/8_anti_sre.xml</br>labs/software_and_malware_analysis/9_malware_behaviour.xml
|
||||
Attacks and exploitation | labs/introducing_attacks/2_malware_msf_payloads.xml</br>labs/introducing_attacks/3_vulnerabilities.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/introducing_attacks/7_post-exploitation.xml</br>labs/introducing_attacks/8_vulnerability_analysis.xml</br>labs/labtainers/bufoverflow.xml</br>labs/labtainers/formatstring.xml</br>labs/labtainers/metasploit.xml</br>labs/labtainers/retlibc.xml</br>labs/software_security_exploitation/4_exploit_development.xml</br>labs/software_security_exploitation/5_linux_bof_format.xml</br>labs/software_security_exploitation/6_linux_stack_bof.xml</br>labs/software_security_exploitation/7_linux_nx_bypass.xml</br>labs/software_security_exploitation/8_linux_aslr_bypass.xml
|
||||
Malicious Activities by Malware | labs/introducing_attacks/5_scanning.xml</br>labs/introducing_attacks/6_exploitation.xml</br>labs/introducing_attacks/7_post-exploitation.xml</br>labs/labtainers/metasploit.xml
|
||||
MALCODE/MALWARE | labs/labtainers/acl-hackerbot-flags.xml</br>labs/labtainers/acl.xml
|
||||
Malware Detection | labs/labtainers/snort.xml</br>labs/response_and_investigation/4_ids.xml</br>labs/response_and_investigation/5_ids_rules.xml</br>labs/response_and_investigation/7_live_analysis.xml</br>labs/response_and_investigation/8_dead_analysis.xml
|
||||
|
||||
# F
|
||||
|
||||
## F Scenarios
|
||||
labs/labtainers/file-deletion.xml</br>labs/labtainers/file-integrity.xml</br>labs/labtainers/macs-hash.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/packet-introspection.xml</br>labs/labtainers/pass-crack.xml</br>labs/labtainers/pcapanalysis.xml</br>labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml</br>labs/response_and_investigation/7_live_analysis.xml</br>labs/response_and_investigation/8_dead_analysis.xml
|
||||
|
||||
## F Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Operating System Analysis | labs/labtainers/file-deletion.xml</br>labs/labtainers/file-integrity.xml</br>labs/response_and_investigation/8_dead_analysis.xml
|
||||
Artifact Analysis | labs/labtainers/macs-hash.xml</br>labs/labtainers/onewayhash.xml</br>labs/labtainers/pass-crack.xml</br>labs/response_and_investigation/2_integrity_detection.xml</br>labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
Main Memory Forensics | labs/labtainers/packet-introspection.xml</br>labs/labtainers/pcapanalysis.xml</br>labs/response_and_investigation/7_live_analysis.xml
|
||||
|
||||
# CPS
|
||||
|
||||
## CPS Scenarios
|
||||
labs/labtainers/iptables-ics.xml</br>labs/labtainers/plc-app.xml</br>labs/labtainers/plc-forensics-adv.xml</br>labs/labtainers/plc-forensics.xml</br>labs/labtainers/plc.xml</br>labs/labtainers/softplc.xml</br>labs/labtainers/softplc2.xml</br>labs/labtainers/ssl.xml
|
||||
|
||||
## CPS Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Cyber-Physical Systems Domains | labs/labtainers/iptables-ics.xml</br>labs/labtainers/plc-app.xml</br>labs/labtainers/plc-forensics-adv.xml</br>labs/labtainers/plc-forensics.xml</br>labs/labtainers/plc.xml</br>labs/labtainers/softplc.xml</br>labs/labtainers/softplc2.xml</br>labs/labtainers/ssl.xml
|
||||
Cyber-Physical Systems | labs/labtainers/iptables-ics.xml</br>labs/labtainers/plc-app.xml</br>labs/labtainers/plc-forensics-adv.xml</br>labs/labtainers/plc-forensics.xml</br>labs/labtainers/plc.xml</br>labs/labtainers/softplc.xml</br>labs/labtainers/softplc2.xml</br>labs/labtainers/ssl.xml
|
||||
|
||||
# WAM
|
||||
|
||||
## WAM Scenarios
|
||||
labs/labtainers/iptables-ics.xml</br>labs/labtainers/iptables.xml</br>labs/labtainers/iptables2.xml
|
||||
|
||||
## WAM Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
FIREWALLS | labs/labtainers/iptables-ics.xml</br>labs/labtainers/iptables.xml</br>labs/labtainers/iptables2.xml
|
||||
|
||||
# HF
|
||||
|
||||
## HF Scenarios
|
||||
labs/labtainers/ssl.xml
|
||||
|
||||
## HF Scenarios by Topics
|
||||
| Topic | Scenario |
|
||||
| --- | --- |
|
||||
Fitting the Task to the Human | labs/labtainers/ssl.xml
|
||||
|
||||
# By Scenario
|
||||
|
||||
|
||||
## examples/cybok_example.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); Unix File Permissions || C | Cryptography | stream ciphers; substitution ciphers |
|
||||
|
||||
|
||||
## examples/cybok_example_no_systems.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); Unix File Permissions || C | Cryptography | stream ciphers; substitution ciphers |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_1_authentication.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | identity management; user authentication; facets of authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) || OSVS | Primitives for Isolation and Mediation | authentication and identification; Linux authentication; Types of user accounts |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_2_pam.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | identity management; user authentication; facets of authentication || OSVS | Primitives for Isolation and Mediation | authentication and identification; Linux authentication; Authentication frameworks (PAM) |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_3_access_controls.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; enforcing access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); Vulnerabilities and attacks on access control misconfigurations || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; filesystems; inodes; and commands; umask || OSVS | Role of Operating Systems | mediation |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_4_suid.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; Elevated privileges; Real and effective identity; Vulnerabilities and attacks on access control misconfigurations || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; setuid/setgid; Hardlink protections |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_5_facls.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; ACCESS CONTROL LIST (ACL); Vulnerabilities and attacks on access control misconfigurations || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Linux Extended Access Control Lists (facl) |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_6_containers.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | SANDBOX; Application-based access controls: user-based access controls insufficiently limit privileges || OSVS | Primitives for Isolation and Mediation | capabilities; Container-based sandboxes: chroot; Docker; Rule-based controls: Course grained: Linux capabilities; Vulnerabilities and attacks on sandboxing misconfigurations || OSVS | Role of Operating Systems | isolation; CONTAINERS || WMS | Fundamental Concepts and Approaches | sandboxing |
|
||||
|
||||
|
||||
## labs/authentication_and_access_controls/ads_7_apparmor.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL); ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL); Application-based access controls: user-based access controls insufficiently limit privileges; Rule-based sandboxes || OSVS | Primitives for Isolation and Mediation | Rule-based controls: Fine grained: AppArmor; Vulnerabilities and attacks on sandboxing misconfigurations || SS | Mitigating Exploitation | limiting privileges |
|
||||
|
||||
|
||||
## labs/introducing_attacks/1_intro_linux.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Protocols and Vulnerability | common network attacks || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS |
|
||||
|
||||
|
||||
## labs/introducing_attacks/2_malware_msf_payloads.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Taxonomy | dimensions; kinds || MAT | Malware Analysis | anti-analysis and evasion techniques || MAT | Attacks and exploitation | EXPLOITATION FRAMEWORKS || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION |
|
||||
|
||||
|
||||
## labs/introducing_attacks/3_vulnerabilities.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION |
|
||||
|
||||
|
||||
## labs/introducing_attacks/4_dns_footprinting.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | PENETRATION TESTING | PENETRATION TESTING - DNS ZONE TRANSFER; EXPLOITATION FRAMEWORKS || SOIM | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - RECONNAISSANCE; PENETRATION TESTING - SOFTWARE TOOLS |
|
||||
|
||||
|
||||
## labs/introducing_attacks/5_scanning.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malicious Activities by Malware | cyber kill chain || NS | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - FINGERPRINTING; PENETRATION TESTING - NETWORK MAPPING - NMAP; PENETRATION TESTING - NETWORK MAPPING - PING || SOIM | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - RECONNAISSANCE; PENETRATION TESTING - SOFTWARE TOOLS |
|
||||
|
||||
|
||||
## labs/introducing_attacks/6_exploitation.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malicious Activities by Malware | cyber kill chain || SS | Categories of Vulnerabilities | CVEs and CWEs || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION |
|
||||
|
||||
|
||||
## labs/introducing_attacks/7_post-exploitation.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malicious Activities by Malware | cyber kill chain; attack on confidentiality; integrity; availability || MAT | Attacks and exploitation | Post-exploitation: pivoting attacks; information gathering || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION |
|
||||
|
||||
|
||||
## labs/introducing_attacks/8_vulnerability_analysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | PENETRATION TESTING | VULNERABILITY ANALYSIS / VULNERABILITY SCANNING; AUDIT APPROACH; PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION || MAT | Attacks and exploitation | EXPLOITATION |
|
||||
|
||||
|
||||
## labs/labtainers/acl-hackerbot-flags.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; enforcing access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); Vulnerabilities and attacks on access control misconfigurations || MAT | MALCODE/MALWARE | trojan; backdoor; TROJANS - BACKDOOR || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; filesystems; inodes; and commands; umask || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Linux Extended Access Control Lists (facl) || OSVS | Role of Operating Systems | mediation |
|
||||
|
||||
|
||||
## labs/labtainers/acl.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; enforcing access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); Vulnerabilities and attacks on access control misconfigurations || MAT | MALCODE/MALWARE | trojan; backdoor; TROJANS - BACKDOOR || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; filesystems; inodes; and commands; umask || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Linux Extended Access Control Lists (facl) || OSVS | Role of Operating Systems | mediation |
|
||||
|
||||
|
||||
## labs/labtainers/arp-spoof.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Protocols and Vulnerability | ADDRESS RESOLUTION PROTOCOL(ARP); ARP (ADDRESS RESOLUTION PROTOCOL); ARP SPOOFING; MITM (MAN-IN-THE-MIDDLE ATTACK); MAN-IN-THE-MIDDLE ATTACK (MITM); ATTACK(S) - ARP || SOIM | Monitor: Data Sources | network traffic |
|
||||
|
||||
|
||||
## labs/labtainers/backups.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Execute: Mitigation and Countermeasures | Recover data and services after an incident; BACKUP - DIFFERENTIAL; BACKUP - INFERENTIAL || SOIM | INCIDENT RESPONSE | RECOVERY - BACKUPS; RECOVERY; BACKUPS |
|
||||
|
||||
|
||||
## labs/labtainers/backups2.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Execute: Mitigation and Countermeasures | Recover data and services after an incident; BACKUP - DIFFERENTIAL; BACKUP - INFERENTIAL || SOIM | INCIDENT RESPONSE | RECOVERY - BACKUPS; RECOVERY; BACKUPS |
|
||||
|
||||
|
||||
## labs/labtainers/bufoverflow.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development || SS | Mitigating Exploitation | ASLR (ADDRESS SPACE LAYOUT RANDOMIZATION); NON-EXECUTABLE MEMORY |
|
||||
|
||||
|
||||
## labs/labtainers/capabilities.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| OSVS | Primitives for Isolation and Mediation | capabilities; Rule-based controls: Course grained: Linux capabilities || SOIM | Monitor: Data Sources | network traffic |
|
||||
|
||||
|
||||
## labs/labtainers/centos-log.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | application logs: web server logs and files; system and kernel logs; Syslog |
|
||||
|
||||
|
||||
## labs/labtainers/centos-log2.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | application logs: web server logs and files; system and kernel logs; Syslog |
|
||||
|
||||
|
||||
## labs/labtainers/cyberciege.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | application logs: web server logs and files; system and kernel logs; Syslog |
|
||||
|
||||
|
||||
## labs/labtainers/denyhost.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Defence Tools | packet filters; intrusion detection systems; intrusion prevention systems || SOIM | Execute: Mitigation and Countermeasures | intrusion prevention systems || SOIM | CM (CONFIGURATION MANAGEMENT) | SSH (SECURE SHELL) |
|
||||
|
||||
|
||||
## labs/labtainers/dmz-example.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Defence Tools | DEMILITARISED ZONE (DMZ) |
|
||||
|
||||
|
||||
## labs/labtainers/dmz-lab.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Defence Tools | DEMILITARISED ZONE (DMZ) |
|
||||
|
||||
|
||||
## labs/labtainers/file-deletion.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Operating System Analysis | storage forensics; data recovery and file content carving |
|
||||
|
||||
|
||||
## labs/labtainers/file-integrity.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | access control; Protecting integrity || F | Operating System Analysis | cryptographic hashing; storage forensics; data recovery and file content carving || SOIM | Monitor: Data Sources | MONITORING - FILE INTEGRITY CHECKERS |
|
||||
|
||||
|
||||
## labs/labtainers/formatstring.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Attacks and exploitation | EXPLOITATION; Exploit development; Mitigation bypass: ASLR || SS | Categories of Vulnerabilities | memory management vulnerabilities; Format string attacks |
|
||||
|
||||
|
||||
## labs/labtainers/gdblesson.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/labtainers/ida.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/labtainers/iptables-ics.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems Domains | industrial control systems || CPS | Cyber-Physical Systems | security and privacy concerns || NS | Network Defence Tools | FIREWALLS; IPTables || NS | Internet Architecture | network layer security || WAM | FIREWALLS | FIREWALLS |
|
||||
|
||||
|
||||
## labs/labtainers/iptables.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Defence Tools | FIREWALLS; IPTables || NS | Internet Architecture | network layer security || WAM | FIREWALLS | FIREWALLS |
|
||||
|
||||
|
||||
## labs/labtainers/iptables2.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Defence Tools | FIREWALLS; IPTables || NS | Internet Architecture | network layer security || WAM | FIREWALLS | FIREWALLS |
|
||||
|
||||
|
||||
## labs/labtainers/ldap.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | identity management; user authentication; facets of authentication; authentication in distributed systems || AAA | Authorisation | AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL) || SOIM | Monitor: Data Sources | network traffic |
|
||||
|
||||
|
||||
## labs/labtainers/local-dns.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Protocols and Vulnerability | ADDRESS RESOLUTION PROTOCOL(ARP); ARP (ADDRESS RESOLUTION PROTOCOL); ARP SPOOFING; DNS ATTACKS |
|
||||
|
||||
|
||||
## labs/labtainers/macs-hash.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) || C | Public-Key Cryptography | symmetric encryption and authentication; MESSAGE AUTHENTICATION CODE (MAC); HASHED MESSAGE AUTHENTICATION CODE (HMAC) || F | Artifact Analysis | cryptographic hashing |
|
||||
|
||||
|
||||
## labs/labtainers/metasploit.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malicious Activities by Malware | cyber kill chain || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS || SOIM | PENETRATION TESTING | PENETRATION TESTING - SOFTWARE TOOLS; PENETRATION TESTING - ACTIVE PENETRATION |
|
||||
|
||||
|
||||
## labs/labtainers/nix-commands.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control || NS | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - PING |
|
||||
|
||||
|
||||
## labs/labtainers/nmap-discovery.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - FINGERPRINTING; PENETRATION TESTING - NETWORK MAPPING - NMAP |
|
||||
|
||||
|
||||
## labs/labtainers/nmap-ssh.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | PENETRATION TESTING | PENETRATION TESTING - NETWORK MAPPING - FINGERPRINTING; PENETRATION TESTING - NETWORK MAPPING - NMAP || SOIM | CM (CONFIGURATION MANAGEMENT) | SSH (SECURE SHELL) |
|
||||
|
||||
|
||||
## labs/labtainers/onewayhash.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) || C | Public-Key Cryptography | symmetric encryption and authentication; MESSAGE AUTHENTICATION CODE (MAC) || F | Artifact Analysis | cryptographic hashing |
|
||||
|
||||
|
||||
## labs/labtainers/packet-introspection.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Main Memory Forensics | network connections; data recovery and file content carving || SOIM | Monitor: Data Sources | network traffic |
|
||||
|
||||
|
||||
## labs/labtainers/pass-crack.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Artifact Analysis | cryptographic hashing || SS | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
|
||||
|
||||
|
||||
## labs/labtainers/pcapanalysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Main Memory Forensics | network connections || NS | OSI (OPEN SYSTEM INTERCONNECT) MODEL | APPLICATION LAYER; DATA LINK LAYER; NETWORK LAYER || SOIM | Monitor: Data Sources | network traffic |
|
||||
|
||||
|
||||
## labs/labtainers/plc-app.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/plc-forensics-adv.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/plc-forensics.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/plc.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/pubkey.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| C | Schemes | TLS || NS | Internet Architecture | transport layer security |
|
||||
|
||||
|
||||
## labs/labtainers/radius.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authentication | identity management; user authentication; facets of authentication; authentication in distributed systems || NS | Internet Architecture | link layer security |
|
||||
|
||||
|
||||
## labs/labtainers/remote-dns.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Network Protocols and Vulnerability | ADDRESS RESOLUTION PROTOCOL(ARP); ARP (ADDRESS RESOLUTION PROTOCOL); ARP SPOOFING; DNS ATTACKS |
|
||||
|
||||
|
||||
## labs/labtainers/retlibc.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || SS | Mitigating Exploitation | NON-EXECUTABLE MEMORY || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development; Mitigation bypass: non-executable memory |
|
||||
|
||||
|
||||
## labs/labtainers/routing-basics.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Internet Architecture | network layer security |
|
||||
|
||||
|
||||
## labs/labtainers/routing-basics2.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| NS | Internet Architecture | network layer security |
|
||||
|
||||
|
||||
## labs/labtainers/setuid-env.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; Elevated privileges; Real and effective identity; Vulnerabilities and attacks on access control misconfigurations || OSVS | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; setuid/setgid |
|
||||
|
||||
|
||||
## labs/labtainers/snort.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | network traffic || SOIM | Analyse: Analysis Methods | misuse detection; anomaly detection || SOIM | Execute: Mitigation and Countermeasures | intrusion prevention systems || NS | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation || MAT | Malware Detection | attack detection |
|
||||
|
||||
|
||||
## labs/labtainers/softplc.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/softplc2.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems |
|
||||
|
||||
|
||||
## labs/labtainers/sql-inject.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | Web vulnerabilities / OWASP Top 10; API vulnerabilities || SS | Prevention of Vulnerabilities | coding practices; Protecting against session management attacks; XSS; SQLi; CSRF; API design || WMS | Server-Side Vulnerabilities and Mitigations | injection vulnerabilities; server-side misconfiguration and vulnerable components; SQL-INJECTION |
|
||||
|
||||
|
||||
## labs/labtainers/ssh-agent.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| C | Public-Key Cryptography | public-key encryption; public-key signatures |
|
||||
|
||||
|
||||
## labs/labtainers/sshlab.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| C | Public-Key Cryptography | public-key encryption; public-key signatures |
|
||||
|
||||
|
||||
## labs/labtainers/ssl.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| C | Public-Key Cryptography | public-key encryption; public-key signatures || CPS | Cyber-Physical Systems | characteristics; security and privacy concerns || CPS | Cyber-Physical Systems Domains | industrial control systems || HF | Fitting the Task to the Human | device capabilities and limitations |
|
||||
|
||||
|
||||
## labs/response_and_investigation/1_integrity_protection.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| AAA | Authorisation | access control; Protecting integrity || OSVS | Primitives for Isolation and Mediation | Linux read only protections: ro mounts; file attributes |
|
||||
|
||||
|
||||
## labs/response_and_investigation/2_integrity_detection.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Artifact Analysis | cryptographic hashing || SOIM | Monitor: Data Sources | MONITORING - FILE INTEGRITY CHECKERS || OSVS | OS Hardening | code and data integrity checks |
|
||||
|
||||
|
||||
## labs/response_and_investigation/3_backups_and_recovery.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Execute: Mitigation and Countermeasures | Recover data and services after an incident; BACKUP - DIFFERENTIAL; BACKUP - INFERENTIAL |
|
||||
|
||||
|
||||
## labs/response_and_investigation/4_ids.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | network traffic || SOIM | Analyse: Analysis Methods | misuse detection; anomaly detection || SOIM | Execute: Mitigation and Countermeasures | intrusion prevention systems || NS | Network Defence Tools | packet filters; intrusion detection systems || MAT | Malware Detection | attack detection |
|
||||
|
||||
|
||||
## labs/response_and_investigation/5_ids_rules.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SOIM | Monitor: Data Sources | network traffic || SOIM | Analyse: Analysis Methods | misuse detection; anomaly detection || NS | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation || MAT | Malware Detection | attack detection |
|
||||
|
||||
|
||||
## labs/response_and_investigation/6_exfiltration_detection.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Artifact Analysis | cryptographic hashing || SOIM | Monitor: Data Sources | network traffic || SOIM | Analyse: Analysis Methods | Exfiltation detection / data loss prevention || NS | Network Defence Tools | packet filters; intrusion detection systems; intrusion prevention systems; IDS rules creation |
|
||||
|
||||
|
||||
## labs/response_and_investigation/7_live_analysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Main Memory Forensics | process information; file information; network connections; artifacts and fragments; challenges of live forensics || OSVS | OS Hardening | anomaly detection || AAA | Accountability | The fallibility of digital evidence to tampering || MAT | Malware Detection | identifying the presence of malware |
|
||||
|
||||
|
||||
## labs/response_and_investigation/8_dead_analysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| F | Operating System Analysis | storage forensics; data recovery and file content carving; Timeline analysis || MAT | Malware Detection | identifying the presence of malware || AAA | Accountability | The fallibility of digital evidence to tampering |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/1_dynamic_and_static_analysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Taxonomy | dimensions; kinds || MAT | Malware Analysis | analysis techniques; analysis environments |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/3_c_and_asm.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/4_asm.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/5_ghidra.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/6_ghidra_analysis.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/6_ghidra_with_live_malware_samples.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/7_dynamic.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/8_anti_sre.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Analysis | analysis techniques; analysis environments; anti-analysis and evasion techniques |
|
||||
|
||||
|
||||
## labs/software_and_malware_analysis/9_malware_behaviour.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| MAT | Malware Taxonomy | dimensions; kinds || MAT | Malware Analysis | analysis techniques; analysis environments |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/1_c_asm_iof.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | Integer overflow || SS | Prevention of Vulnerabilities | language design and type systems |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/2_race_conditions_format_str.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | race condition vulnerabilities; structured output generation vulnerabilities; Format string attacks || SS | Prevention of Vulnerabilities | race condition mitigations; structured output generations mitigations |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/3_bug_hunting_and_fuzzing.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Detection of Vulnerabilities | dynamic detection |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/4_exploit_development.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/5_linux_bof_format.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows; Format string attacks || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/6_linux_stack_bof.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/7_linux_nx_bypass.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || SS | Mitigating Exploitation | NON-EXECUTABLE MEMORY || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development; Mitigation bypass: non-executable memory |
|
||||
|
||||
|
||||
## labs/software_security_exploitation/8_linux_aslr_bypass.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| SS | Categories of Vulnerabilities | memory management vulnerabilities; Stack smashing buffer overflows || SS | Mitigating Exploitation | ASLR (ADDRESS SPACE LAYOUT RANDOMIZATION) || MAT | Attacks and exploitation | EXPLOITATION; EXPLOITATION FRAMEWORKS; Exploit development; Metasploit Framework development; Mitigation bypass: ASLR |
|
||||
|
||||
|
||||
## labs/web_security/websec_lab.xml
|
||||
| KA | Topic | Keywords
|
||||
| --- | --- | --- |
|
||||
| WMS | Fundamental Concepts and Approaches | web PKI and HTTPS; authentication; cookies; passwords and alternatives; JAVASCRIPT / HYPERTEXT MARKUP LANGUAGE (HTML) / CASCADING STYLE SHEETS (CSS) / HYPERTEXT TRANSFER PROTOCOL (HTTP)\n\t\tCOOKIES; HYPERTEXT TRANSFER PROTOCOL (HTTP) - PROXYING; Broken Access Control / Insecure Direct Object References; SESSION HIJACKING; REPRESENTATIONAL STATE TRANSFER (REST) || WMS | Client-Side Vulnerabilities and Mitigations | client-side storage; CLIENT-SIDE VALIDATION; clickjacking || WMS | Client-Side Vulnerabilities and Mitigations | client-side storage; CLIENT-SIDE VALIDATION; clickjacking || WMS | Server-Side Vulnerabilities and Mitigations | injection vulnerabilities; server-side misconfiguration and vulnerable components; CROSS-SITE SCRIPTING (XSS); SAME ORIGIN POLICY (SOP); COMMAND INJECTION; SQL-INJECTION; CROSS-SITE REQUEST FORGERY (CSRF); CONFUSED DEPUTY ATTACKS || SS | Categories of Vulnerabilities | Web vulnerabilities / OWASP Top 10; API vulnerabilities || SS | Prevention of Vulnerabilities | coding practices; Protecting against session management attacks; XSS; SQLi; CSRF; API design |
|
||||
|
||||
|
||||
Reference in New Issue
Block a user