mirror of
https://github.com/billbuchanan/appliedcrypto.git
synced 2026-02-21 11:18:02 +00:00
Update README.md
This commit is contained in:
@@ -642,31 +642,31 @@ Using an Internet search, list ten other encryption algorithms which can be used
|
||||
You should have access to your AWS Learner Lab, and where we will use AWS KMS (Key Management System) to generate encryption keys, and use symmetric key encryption. With symmetric key encryption, Bob and Alice use the same encryption key to encrypt and decrypt. In the following case, Bob and Alice share the same encryption key, and where Bob encrypts plaintext to produce ciphertext. Alice then decrypts with the same key, in order to recover the plaintext:</p>
|
||||
|
||||
|
||||
 {width=50% }
|
||||

|
||||
|
||||
Normally we use AES encryption for this. Initially in KMS, we create a new key within our Customer managed keys:
|
||||
|
||||
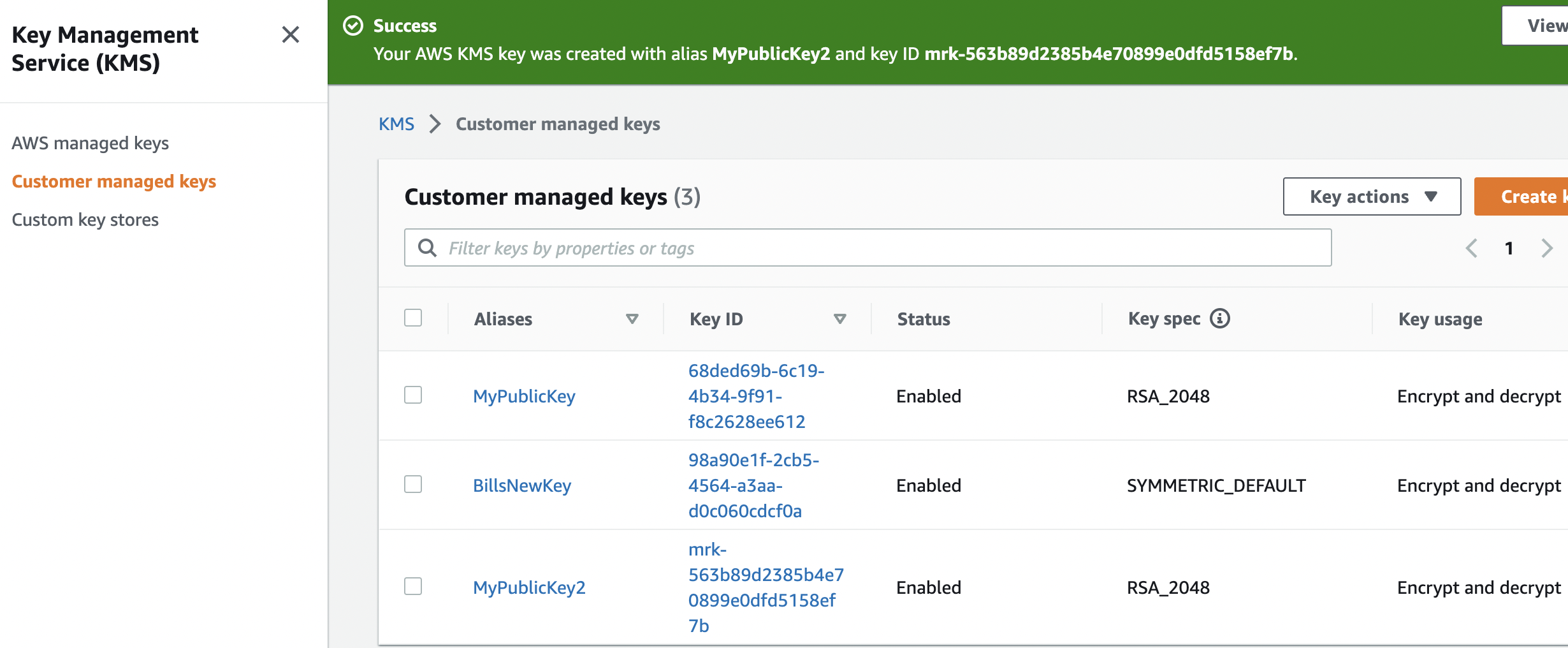 {width=50% }
|
||||

|
||||
|
||||
and then create the key:
|
||||
|
||||
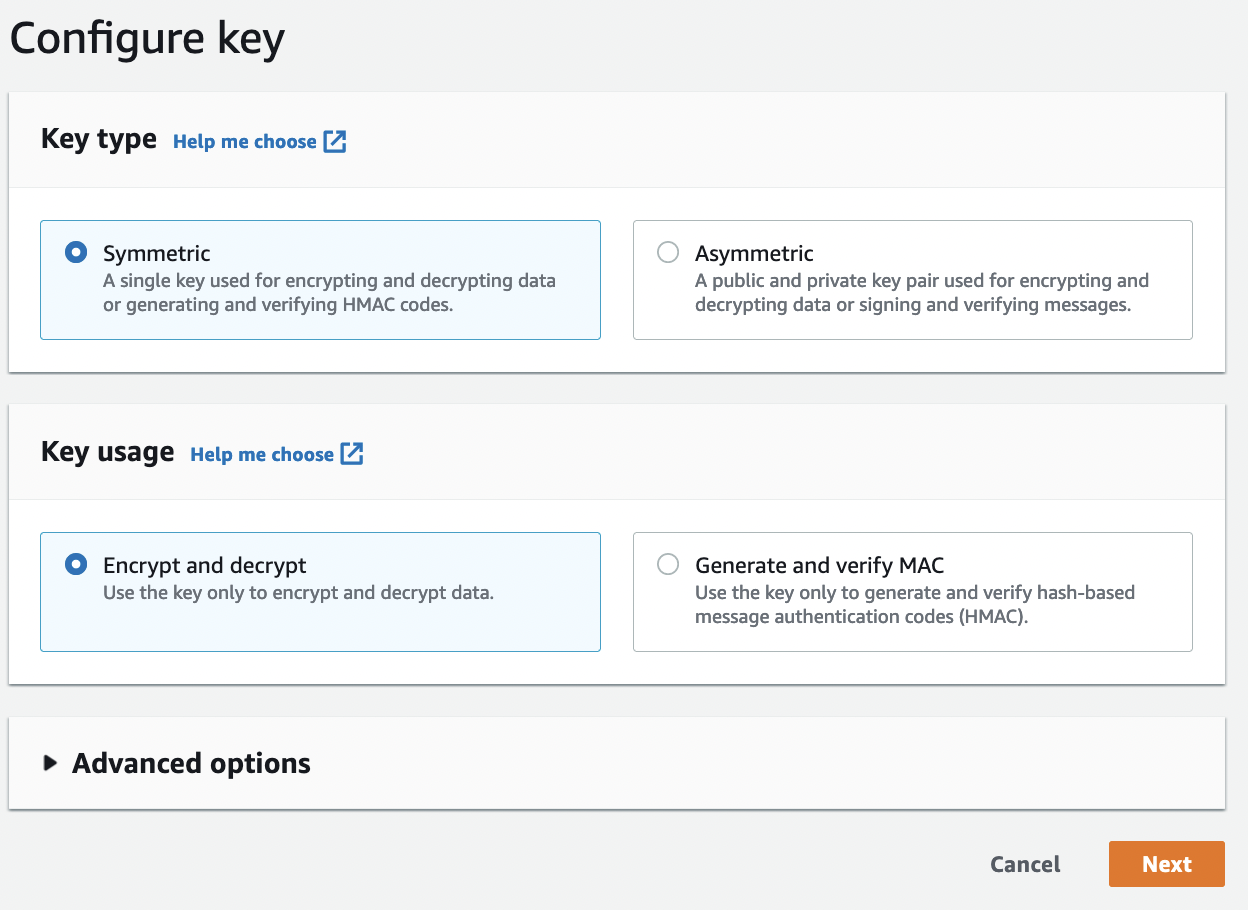 {width=50% }
|
||||

|
||||
|
||||
|
||||
|
||||
Next, we give it a name:
|
||||
|
||||
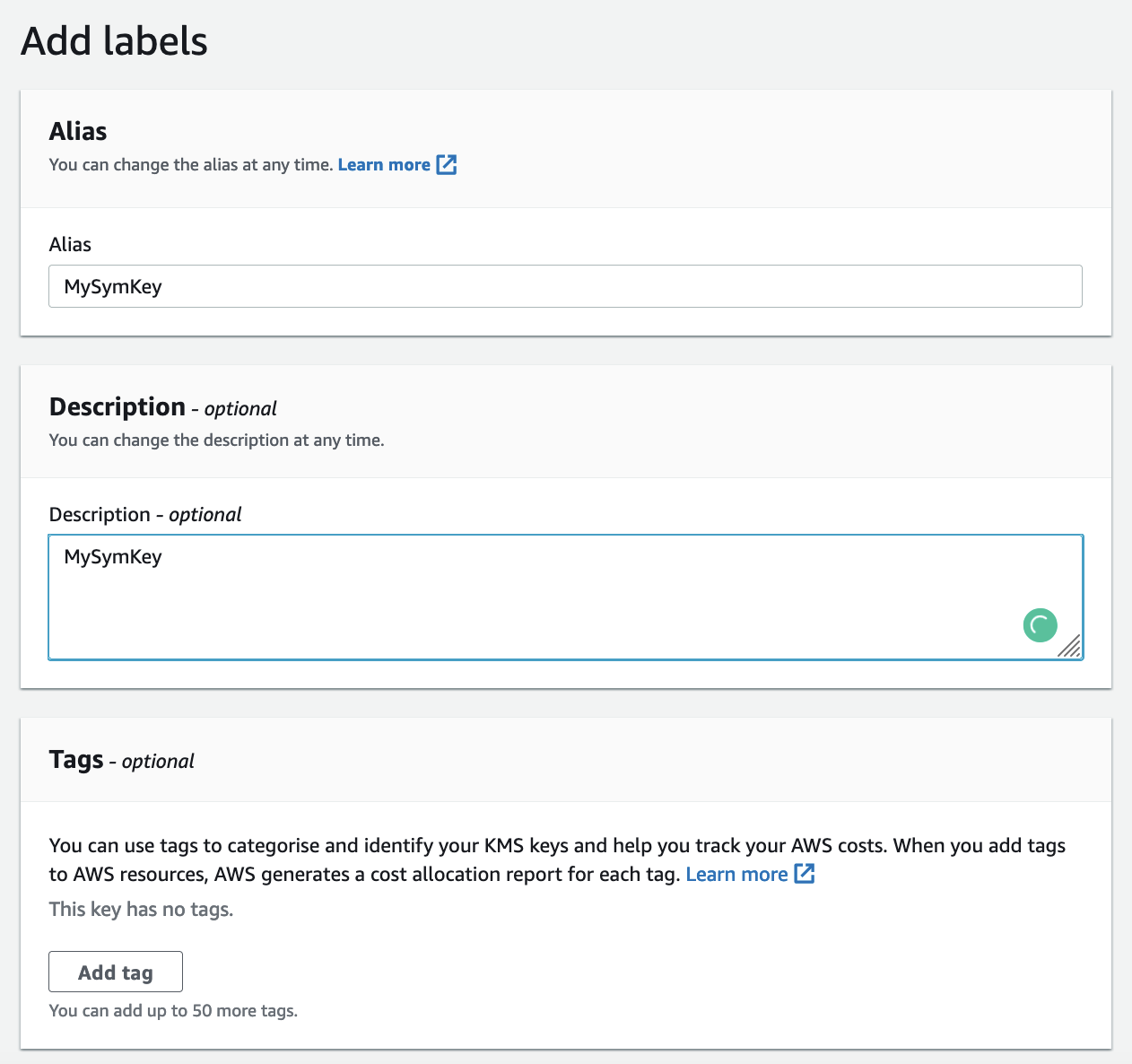 {width=50% }
|
||||

|
||||
|
||||
|
||||
And then define the administrative permission (those who can delete it):
|
||||
|
||||
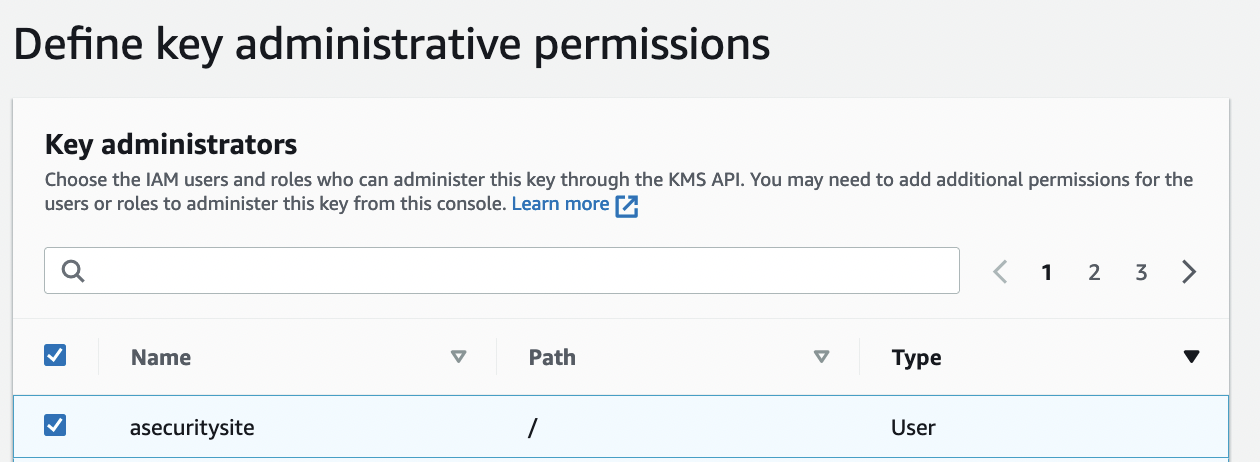 {width=50% }
|
||||

|
||||
|
||||
|
||||
And the usage:
|
||||
|
||||
 {width=50% }
|
||||

|
||||
|
||||
|
||||
The policy is then:
|
||||
|
||||
Reference in New Issue
Block a user