34 KiB
Lecture Videos and CyBOK
The Cyber Security Body of Knowledge (CyBOK) is a body of knowledge that aims to encapsulate the various knowledge areas present within cyber security. Scenarios within SecGen now contain XML elements linking them to CyBOK knowledge areas and specific topics within those knowledge areas. Additionally, video lectures for scenarios are tagged with their CyBOK associations.
This file is an autogenerated index of the lecture videos referenced by scenarios -- with CyBOK metadata.
There are 70 videos with CyBOK metadata.
Cyber Securtiy Body of Knowledge (CyBOK) Issue 1.0 is Crown Copyright, The National Cyber Security Centre 2021, licensed under the Open Government Licence http://www.nationalarchives.gov.uk/doc/open-government-licence/.
Lecture Videos
User accounts and Linux
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication; Types of user accounts |
Passwords Part 1 Hashing and salt
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
Passwords Part 2 Attacks and Countermeasures
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
Password cracking with Johnny
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | user authentication; Cryptography and authentication (hashes and attacks against authentication schemes / passwords) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
Authentication
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | authentication and identification; Linux authentication |
Biometrics
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication; AUTHENTICATION - BIOMETRICS |
Authentication Tokens and One-Time Passwords
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; user authentication; facets of authentication; AUTHENTICATION - OTP (ONE-TIME PASSWORD); AUTHENTICATION - TOKENS |
Network-based Authentication (SSO, AD, LDAP, Kerberos)
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHORIZATION - SSO (SINGLE SIGN-ON); AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL); AUTHENTICATION - KERBEROS; ACTIVE DIRECTORY DOMAIN SERVICES (ADDS) |
| Authentication, Authorisation & Accountability (AAA) | Access Control in Distributed Systems | core concepts; federated access control |
Lightweight Directory Access Protocol (LDAP)
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | theory; Network based-authentication with heterogeneous Linux and Windows networks; AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL) |
Kerberos overview
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHENTICATION - KERBEROS |
Active Directory
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authentication | identity management; authentication in distributed systems; user authentication; Network based-authentication with heterogeneous Linux and Windows networks |
| Authentication, Authorisation & Accountability (AAA) | Authorisation | AUTHORIZATION - SSO (SINGLE SIGN-ON); AUTHORIZATION - LDAP (LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL); AUTHENTICATION - KERBEROS; ACTIVE DIRECTORY DOMAIN SERVICES (ADDS) |
| Authentication, Authorisation & Accountability (AAA) | Access Control in Distributed Systems | core concepts; federated access control |
Access Controls: Introduction
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; enforcing access control; theory |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | mediation; TRUSTED COMPUTING BASE (TCB); REFERENCE MONITOR |
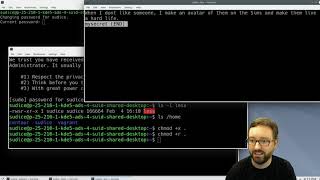
Unix File Permissions
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; enforcing access control; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL) |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; filesystems; inodes; and commands |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | mediation |
Access Control Models
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; theory; ACCESS CONTROL - DAC (DISCRETIONARY ACCESS CONTROL); ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL); ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL); ACCESS CONTROL - ROLE-BASED |
| Operating Systems & Virtualisation (OSV) | OS Security Principles | security models |
Special File Permissions SetUID, SetGUI
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; Elevated privileges; Real and effective identity; Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Unix File Permissions; setuid/setgid |
ACLs and Capabilities
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; ACCESS CONTROL - MATRIX; ACCESS CONTROL LIST (ACL); Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | capabilities |
Linux Extended ACLs
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; ACCESS CONTROL LIST (ACL); Vulnerabilities and attacks on access control misconfigurations |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Access controls and operating systems; Linux security model; Linux Extended Access Control Lists (facl) |
Sandboxing and Virtualisation
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | SANDBOX; Application-based access controls: user-based access controls insufficiently limit privileges |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | capabilities; Container-based sandboxes: chroot; Docker; Rule-based controls: Course grained: Linux capabilities; System-level sandboxes (complete OS; Qubes); hardware-emulation and paravirtualisation; Copy on write sandboxes |
| Operating Systems & Virtualisation (OSV) | Role of Operating Systems | isolation; CONTAINERS |
| Web & Mobile Security (WAM) | Fundamental Concepts and Approaches | sandboxing; permission dialog based access control |
Rule-based Sandboxing and Mandatory Access Controls
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | ACCESS CONTROL - MAC (MANDATORY ACCESS CONTROL); ACCESS CONTROL - NDAC (NON-DISCRETIONARY ACCESS CONTROL); Application-based access controls: user-based access controls insufficiently limit privileges; Rule-based sandboxes; System call interposition; Integrity level access controls |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Rule-based controls: Fine grained: AppArmor |
| Software Security (SS) | Mitigating Exploitation | limiting privileges |
The CIA Triad
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=sv1pHuuoW9g
| KA | Topics | Keywords |
|---|---|---|
| (IC) | Foundational Concepts | objectives of cyber security |
Protecting Integrity
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=grISRv-CuHE
| KA | Topics | Keywords |
|---|---|---|
| Authentication, Authorisation & Accountability (AAA) | Authorisation | access control; Protecting integrity |
| Operating Systems & Virtualisation (OSV) | Primitives for Isolation and Mediation | Linux read only protections: ro mounts; file attributes |
Monitoring Integrity
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=qzyEdeQ_7ZY
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Artifact Analysis | cryptographic hashing |
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | MONITORING - FILE INTEGRITY CHECKERS |
| Operating Systems & Virtualisation (OSV) | OS Hardening | code and data integrity checks |
Incident Response
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=kz7m-iyzSOw
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | Fundamental Concepts | workflows and vocabulary; architectural principles |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; handle: actual incident response; follow up: post incident activities; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE; incident response methodologies |
| Law & Regulation (LR) | Data Protection | investigation and prevention of crime; personal data breach notification; enforcement and penalties |
Contingency Planning
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE |
Backup Planning
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | Recover data and services after an incident |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning; BUSINESS CONTINUITY PLAN - AND INCIDENT RESPONSE |
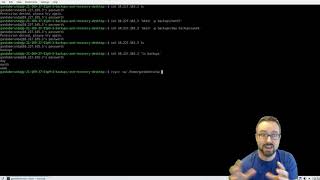
Backup Levels: Differential and Incremental Backups Using Rsync
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | Recover data and services after an incident; BACKUP - DIFFERENTIAL; BACKUP - INFERENTIAL |
| Operating Systems & Virtualisation (OSV) | Human Factors: Incident Management | prepare: incident management planning |
The Cloud
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | DATA REDUNDANCY; REDUNDANCY IN NETWORK SERVICES |
| Distributed Systems Security (DSS) | CLOUD - COMPUTING - SERVICES | CLOUD COMPUTING - DEPLOYMENT MODELS; CLOUD COMPUTING - RESOURCE POOLING; CLOUD COMPUTING - SERVICE MODELS - IAAS; CLOUD COMPUTING - SERVICE MODELS - PAAS; CLOUD COMPUTING - SERVICE MODELS - SAAS; CLOUD COMPUTING - STORAGE |
| Operating Systems & Virtualisation (OSV) | CLOUD - COMPUTING - SERVICES | CLOUD COMPUTING - VIRTUALIZATION |
| Privacy & Online Rights (POR) | Confidentiality | CLOUD COMPUTING - PRIVACY CONCERNS |
Redundancy and RAID
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | DATA REDUNDANCY |
Intrusion Detection and Prevention Systems (IDS IPS)
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
IDS accuracy
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | the base-rate fallacy |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | intrusion detection systems |
Snort IDS
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Security Operations & Incident Management (SOIM) | Execute: Mitigation and Countermeasures | intrusion prevention systems |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
Regexp (unstructured demo)
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (N/A) | Hints | Technical hint |
Snort Regexp Tips
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | network traffic |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | misuse detection; anomaly detection |
| Network Security (NS) | Network Defence Tools | packet filters; intrusion detection systems; IDS rules creation |
| Malware & Attack Technology (MAT) | Malware Detection | attack detection |
Live System Analysis: Concepts
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections; artifacts and fragments; challenges of live forensics |
| Operating Systems & Virtualisation (OSV) | OS Hardening | anomaly detection |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
Live System Analysis: Tools Demo
by Z. Cliffe Schreuders
https://www.youtube.com/watch?v=iUInvMrBw3k
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections; artifacts and fragments; challenges of live forensics |
| Operating Systems & Virtualisation (OSV) | OS Hardening | anomaly detection |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
Investigating a running process
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Main Memory Forensics | process information; file information; network connections |
Dead System Analysis
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Forensics (F) | Operating System Analysis | storage forensics; data recovery and file content carving; Timeline analysis |
| Malware & Attack Technology (MAT) | Malware Detection | identifying the presence of malware |
| Authentication, Authorisation & Accountability (AAA) | Accountability | The fallibility of digital evidence to tampering |
Log Management
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Security Operations & Incident Management (SOIM) | Monitor: Data Sources | system and kernel logs; application logs: web server logs and files; Syslog |
| Security Operations & Incident Management (SOIM) | Analyse: Analysis Methods | contribution of SIEM to analysis and detection |
Reverse Engineering and Malware Analysis: Part 1 Static Analysis
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
Reverse Engineering and Malware Analysis: Part 2 Dynamic Analysis
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
The Problem of Malware
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Taxonomy | potentially unwanted programs |
| Operating Systems & Virtualisation (OSV) | Attacker Model | attack surface; threats to security for modern OSs |
Malware Types
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Taxonomy | dimensions; kinds; potentially unwanted programs |
Stopping Malware
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Detection | ANTI-MALWARE - SYSTEMS; ANTIVIRUS SOFTWARE; MALCODE/MALWARE - COUNTERMEASURES - CODE SIGNING; MALCODE/MALWARE - COUNTERMEASURES - SANDBOXING; MALCODE/MALWARE - THIRD-PARTY CERTIFICATIONS |
Introduction to C - Part 1
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: C |
Introduction to C - Part 2
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: C |
From C to Assembly Language
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Technical Underpinning | Technical underpinnings for malware analysis: ASM; Technical underpinnings for malware analysis: C |
Recognising C Constructs in Assembly
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques |
SRE with Ghidra: Overview and Interface
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
SRE with Ghidra: Analysis and Renaming Variables and Editing Function Signatures
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; STATIC ANALYSIS |
Dynamic Analysis and Debugging
by Thalita Vergilio
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; analysis environments; DYNAMIC ANALYSIS |
Malware Behaviour
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
DLL injection for Linux: LD_PRELOAD Demo
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
Packers and UPX Short Demo
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Malware Analysis | analysis techniques; MALICIOUS ACTIVITIES BY MALWARE |
Software, Vulnerabilities and Exploits
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Attacks and exploitation | EXPLOITATION |
Software Vulnerabilities
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Malware & Attack Technology (MAT) | Attacks and exploitation | EXPLOITATION |
Structured Output Generation Vulnerabilities
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | structured output generation vulnerabilities |
| Software Security (SS) | Prevention of Vulnerabilities | structured output generations mitigations |
Race Conditions and Time of Check to Time of Use TOCTTOU Vulnerabilities
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | race condition vulnerabilities |
| Software Security (SS) | Prevention of Vulnerabilities | race condition mitigations |
The Format String Vulnerability
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | Format string attacks |
Fuzzing Part 1
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Detection of Vulnerabilities | dynamic detection |
Fuzzing Part 2
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Detection of Vulnerabilities | dynamic detection |
Overflows and Stack Smashing Buffer Overflows
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
Writing Exploits (Buffer Overflows Part 2)
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
Memory Vulnerabilities
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Categories of Vulnerabilities | memory management vulnerabilities |
The Stack (part 1)
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Technical Underpinning | Technical underpinnings for memory management vulnerabilities: the stack |
The Stack (part 2)
by Tom Shaw
| KA | Topics | Keywords |
|---|---|---|
| Software Security (SS) | Technical Underpinning | Technical underpinnings for memory management vulnerabilities: the stack |
Threat modeling using STRIDE and Attack Trees
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Prescriptive Processes | Microsoft SDL |
| Risk Management & Governance (RMG) | THREAT ANALYSIS | THREAT MODEL; ATTACK TREES |
STRIDE Threat Modeling using Microsoft Threat Modeling Tool
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Prescriptive Processes | Microsoft SDL |
| Risk Management & Governance (RMG) | THREAT ANALYSIS | THREAT MODEL; ATTACK TREES |
Secure Design Principles
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| Operating Systems & Virtualisation (OSV) | OS Security Principles | Saltzer and Schroeder’s principles; newer principles |
Secure Development Lifecycles
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Motivations for Secure Software Lifecycle | vulnerabilities can be exploited without being noticed |
| (SSL) | Prescriptive Processes | Microsoft SDL; SAFECode; Touchpoints |
Open source development and security practices
by Z. Cliffe Schreuders
| KA | Topics | Keywords |
|---|---|---|
| (SSL) | Prescriptive Processes | Open source secure development |